viernes, 31 de julio de 2009
How to sort a malware collection
Today I´ll discuss the different options we can decide about how to sort our malware collection.
Collection packed or collection unpacked?
I always have considered that having the collection packed is the best decission for multiple reasons. Almost every consideration is a pro for having the collection packed and there are no contras almost; meanwhile having the collection unpacked has lots of contras in my opinion.
Pros of having the collection packed:
* Making backups will be easier.
You create new archives containing new stuff so backups are incremental, no need to backup everything everytime.
* C0llection will take less space on hard disk.
* KAV scans a packed collection as fast as an unpacked one. Some tests even say that it´s faster.
* Verifying the integrity of the collection is easier.
You just need to run the test function of WinZIP to know if everything is ok. Checking if something is wrong with an unpacked collections takes more time as you must run a check of the whole drive storing the collection.
The only contra is the amount of time required to compress new files but as we will compress just a few files every day that´s not relevant.
There are other reasons but I´ll discuss some of them in future posts.
How to name files?
Some traders used to like to name files by the identification given by KAV. I always considered this as a mistake because identifications may be modified so the file name would be wrong.
I consider that it has more advantages having the files named by a hash, like MD5, SHA-1 or SHA-256.
You can use RenFiles to rename files to MD5 or SHA-256.
How to name file extensions?
Using KAV the file extension is not relevant as identification will not change depending if the file has the right extension or not.
Some collectors prefer extensions like .VXE or .VLL instead .EXE and .DLL to avoid infections.
A good collector should be able to manage a collection having the right extensions on files because he manages the files in a safe environment. A safe environment is that one where you can not run a virus or malware accidentally.
If you want to name files by their right extension use RenFiles.
What folder structure should I use to store the collection?
If you decide to follow my tip and keep the collection packed you don´t need a folder structure. Just decide a file size limit for the ZIP (I recommed ZIP to pack) and add new files until you reach the limit. When you reach it continue compressing on next archive. You can use consecutive numbers to name archives. Like:
MALW00001.ZIP
MALW00002.ZIP
MALW00003.ZIP
MALW00004.ZIP
.
.
.
If you decide you want an unpacked collection then continue reading.
Years ago many collectors liked having the folder structure based in the KAV identification name. Something like:
C:\COLLECTION\T\Trojan\Win32\Example\a\FILE.EXE
or
C:\COLLECTION\T\Trojan.Win32.Example.a\FILE.EXE
Several tools were created to process files and copy/move them to such structures using KAV logs.
If you like that folder structure method to sort the collection you can download VS2000 GUI and use it. You can get VS2000 GUI from here.
You have that feature under "Virus organizer" tab.
There are 5 different folder structure types available. You can see examples of how collection will look like clicking in the "?" buttons.
If I´m forced to use a folder structure then the folder structure method I prefer is the one called "Bulk". It´s based in the hash of the file. There is a root folder and inside 16 folders, from 0-9 and A-F. Inside those folders there are other 16 subfolders with the first 2 chars of the hash. 16*16 folders in total. Something like:
C:\MALWARE\0\00
C:\MALWARE\0\01
C:\MALWARE\0\02
.
.
C:\MALWARE\A\A0
C:\MALWARE\A\A1
C:\MALWARE\A\A2
.
.
C:\MALWARE\F\FE
C:\MALWARE\F\FF
This is one of the five available structures in VS2000 GUI.
And that´s all you must decide about how to sort your malware collection. A fast resume:
Decide if you want collection packed or unpacked
Decide how to name files
Decide how to name extensions
If you decide an unpacked collection then decide the folder structure.
My "setup" is:
Collection packed (using ZIP format).
File names by their SHA-256
Files having the right extension
File size for archives: around 200 and 300 MB. More can be problematic for KAV.
File names for archives: VIRUS001.ZIP, VIRUS002.ZIP, etc
And that´s all for now. See you soon!
jueves, 30 de julio de 2009
RenFiles: the file renamer for malware collectors
Today I´ll introduce RenFiles.
RenFiles is a tool (command line) designed to rename file names and file extensions on demand.
This tool is recursive, so you can specify a folder and all files inside will be renamed.
RenFiles is able to rename file names to their CRC32, MD5 or SHA-256 hash depending of the used command.
RenFiles is also able to rename file extensions to the proper of each file with big accuracy.
Having the files named by their proper extension used to be very important because some antivirus were giving a different report depending of the file extension. KAV 4.5 doesn´t have this problem but anyway having files named properly is more "professional".
RenFiles has other features but the most important ones are the described above.
You can find a manual of RenFiles here.
You can get RenFiles binary here.
Next posts will be related to collection storage and sorting methods.
lunes, 27 de julio de 2009
StripLog: the right hand of VS2000
Today I´ll talk about StripLog.
StripLog is a tool designed to work with antivirus logs, specially KAV 4.5 logs.
The main objective of StripLog is to copy/move/delete the files that appear in logs.
Imagine you receive a request from other trader of 100 files. You must take the 100 files from the request, copy them to a folder and pack the files to send. StripLog will do this work for you.
StripLog has the ability to unpack files from ZIP/RAR/7Z files.
StripLog is able to do other tasks like killing empty directories or delete zero byte files.
You can read about all StripLog functions and the manual. Get it from here.
You can get StripLog from here. Inside the RAR package you will find 2 DLLs. You must copy them to %WINDIR%\System32.
There is not much to say about StripLog but it´s really an useful tool for collectors. It makes the work of managing files pretty easy.
sábado, 25 de julio de 2009
File Weeding: Keep clean your collection of duplicate files
Today I will comment about file weeders.
A file weeder is a tool that looks for identical files and by default or on demand deletes them. Some weeders allow the user to choose what duplicate files to delete and what ones to keep.
In terms of malware collecting the most important thing to consider before deciding what file weeder to use is what hash algorithm we want to use.
In the first years of collecting most collectors used ThunderByte Weeder aka TbWeeder. This weeder was done by the same author of ThunderByte Antivirus, Frans Veldman, and it used a CRC16 hash.
Some years later the first collisions (different files having same hash) for CRC16 appeared in virus collections so collectors switched to weeders using CRC32 hashing.
Around year 2000 some collectors started to use MD5 hash and some stayed with CRC32.
After 2000 the story repeats and first CRC32 collisions appear in virus collections. As workaround solution for these CRC32 collisions, two weeders (VirWeed and FWeeder) are created, using CRC32 hashing plus file size checking to verify for duplicates.
At the beginning I thought it was not possible that two different files may have the same CRC32 and file size but this was proved to be wrong. This was the end of the use of CRC32 between virus collectors.
Actually traders use MD5 weeders or SHA-1. Some months ago I decided to change the hash of my file weeder and initially I considered using MD5 but I was told that generating collisions for MD5 was simple so I decided to go with SHA-256.
I´m not aware of MD5 collisions in malware collections so I´ld say that at the moment using a weeder that uses MD5 is safe.
If you decide to use a MD5 weeder I recommend FAST! File Weeder (FWeeder) by my friend Bumblebee. Right now it´s open source.
You can get source code here.
You can get binary here.
I will give a brief description of how to use FWeeder.
FWeeder is a command line tool. Run "fweeder -h" to get the help screen.
To create a database of our collection run: fweeder -c
To add new entries to database (new files you got in your collection) run: fweeder -a
To look for duplicate files run: fweeder -v
By default FWeeder will not delete duplicated files. You must add "-k" switch. Examples:
fweeder -c c:\virus -k
fweeder -a c:\newvirus -k
fweeder -v c:\test -k
With that information you have the basic information to weed your collection.
Old weeders were dangerous when used by inexpert hands. Some collectors deleted their collections because they created a database and then looked for duplicates in their own collection!!!
FWeeder has a "newbie" protection to avoid that situation but anyway it´s always a good idea to make a backup of your collection.
I will make a post exclusively to talk about backups and how important they are but before I do it... make a backup.
miércoles, 22 de julio de 2009
VirSort: long life to the king of the virus collecting tools!
Today I will dedicate my post to the tool that has been more years around virus collectors: VirSort.
VirSort was written many years ago and it has been rewritten by different people several times.
Let´s start with a lesson of history.
Christian Julius is the father of the virus sorting tool called VirSort. Here we can read the documentation he added to the first package he released:
V I R S O R T 1.1 beta
Why you need Virsort?
You collect virii and the collection growed up to a few thousand samples and each week you get another few hundred samples?
Than you have the problem to analyse and sort them into directories spending hours while doing do.
VIRSORT takes this work away from you. It analyzes a scan list from the popular anti-virus program F-Prot by Fridrik Skulason and compares the incoming virii against your own. After doing so it sorts out the dupes and copies the new virii in separate directories.
How to use:
1. Make an F-Prot list of your virii and don't forget to add the /nowrap command line parameter.
2. Copy this list in the same directory as virsort.exe
3. Type virsort -b
virsort.dat = The database
unsort.log = Suspicious files not identified 100% (sort them in manually
new_vir.log = The new virii
trojans.log = Trojan horses
variants.log = New or modified virii
possible.log = Possibly infected files
4. Type in virsort -s
You can use the -sd switch instead to move the files into the target directory, othwise they'll be copied.
Note: The dupes are not removed. I'll fix this in future versions of my software.
5. You get a new collection?
Make a F-Prot file and type
virsort -c
The output file contains the new virii list in binary format.
Go to step 4 to sort them in.
Virsort asks you for updating your database now.
If you type 'y' the incoming virii are added to your database and the old database is deleted.
I can't garantee that there are no bugs in it, if you recognize some please let me know.
This software is published as Public Domain, so you can spread it to everybody who wants it, but you are not allowed to take a fee for it.
Further and improved versions will be published as Shareware.
Please apologize any spelling mistakes.
Christian Julius
Germany
email: chj@ing.ruhr.de
That´s the information the author included in the first release of the package.
It´s not clear if Brian Burdick (Shadow Seeker) continued coding on that version done by Christian Julius or if he started a new version from scratch. Anyway he initiated the second phase of the development. At some point the project went to Jim Fougeron (Poltergeist) hands.
Polt was in charge of the project for some time but around 1997 more or less he left the trading scene. He sent VirSort source code to Spooky but Spooky never continued with the development. This second release of VirSort was coded in C++.
When it was obvious that Spooky was not going to continue working on the tool Brian started a new version of VirSort (third stage in the history of VirSort). This time Brian coded the tool in Pascal and renamed the tool to VirSort 2000 or just VS2000 as it´s better known nowadays.
After a few releases Brian gave up development, a bit because he had not much time and a bit because he considered the tool already had the required features. This happened in 1998.
I was not satisfied with the features as I wanted more included. I asked him the source code to continue improving it. In that moment I had no idea of Pascal. Brian also sent the source code to Ralph Roth. It was supposed that both Ralph and me would continue with the development but finally I was the only one keeping the updating work And that´s how it has been from 1998 to right now.
In the fourth stage I started improving Brian´s code but at some point I rewritten almost from scratch the tool. Initially the tool was being compiled with Turbo Pascal, after a while with Free Pascal and right now it´s being coded in Delphi.
The amount of features is so big that explaining all them would take lots of space. It´s better if I explain the main features and you learn to use the others as you need them. You can find a manual (a bit outdated but still valid) here.
There are 3 main functions: build a database, compare a log and add new stuff to existing database.
Build a database: -B. Example: VS2000 -B AVP.LOG
Compare a log: -C. Exampe: VS2000 -C OTHER_TRADER.LOG
Add new stuff to your database: -A. Example: VS2000 -A AVP2.LOG
Pretty easy to use.
I didn´t mention it before but VirSort always has been a command line tool.
Many traders I have met in my years in the trading scene prefered GUI tools but I must say that most of the best tools for collecting are usually those ones running at command line.
You can find VS2000 for Win32 here.
I also compiled a version of VS2000 for Linux. You can find it here but Linux version is not supported and it has not been tested deeply.
VS2000 is so professional that even people from antivirus vendors have used it. Some of them asked for the inclusion of support of the reports generated with their antivirus.
Enough about VS2000! You better go and try it!
martes, 21 de julio de 2009
KAV 4.5 - The antivirus of the traders
This entry in the blog will be dedicated to the antivirus that all malware collectors use to exchange and that you can use to catalog your collection.
You can download KAV 4.5 from this link.
You launch the installer and the welcome screen appears. Click "Next >".
Now you must choose a temporal folder where KAV will decompress installation files. Click "Next >" when you are done.
Another welcome screen appears. Click "Next >" again. Click "Yes" to accept license agreement. Does anyone in the world read that?
Introduce customer information and click "Next >".
Choose destination folder for KAV and don´t touch the common files folder. Click "Next >".
Select program folder. Default will be fine. Click "Next >".
Choose "Custom" setup type and click "Next >".
Everything must be disabled except: Kaspersky Anti-Virus Core Components, Kaspersky Anti-Virus Bases, Kaspersky Anti-Virus Scanner and Kaspersky Anti-Virus Updater. Click "Next >". Like this:
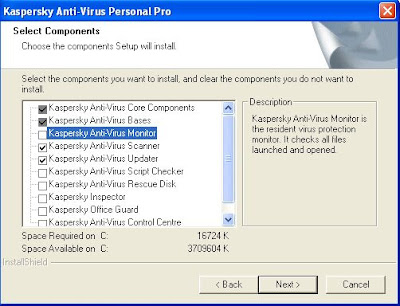
Click "Next >" in the "Start Copying Files" screen.
You can associate report files (*.REP and *.RPT) to KAV´s Report Viewer utility. This is not really necessary and you can skip the association if you want. You must configure where you want to store report files. Click "Next >" when you are done.
Add your valid key file and click "Next >".
Don´t enable the "Launch Kaspersky Anti-Virus Updater" checkbox and click "Finish".
If you pretend to exchange with malware collectors you should run "Kaspersky Anti-Virus Updater" and configure it properly. For this you must do:
In the welcome screen of Kaspersky Anti-Virus Updater enable the "Change settings" checkbox. Click "Next >".
Open "Update Kaspersky Anti-Virus from Internet" tree and click in the "..." button. Select all links and click the "Delete URL" icon. Click in the "Add URL" icon and introduce next link:
http://66.232.119.78/~largefus/AVP/
It will look like this:
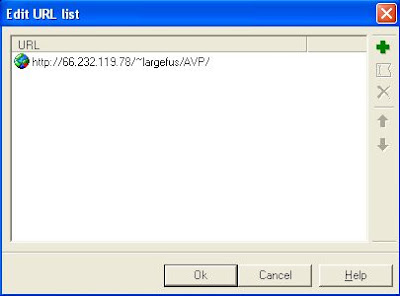
Click "Next >" twice and Kaspersky Anti-Virus should start updating databases. If you receive an error message telling the updater can not obtain contents means that Kaspersy Anti-Virus, for some reason I never was able to understand, will not work. In this case you can try using the KAV Updater tool I coded for this situation. You can retrieve it from here.
If you don´t plan exchanging with collectors you can skip the above steps and update KAV defs using default KAV servers.
You must consider with what periodicity you will update KAV defs. If you use the server used by traders you must know defs are updated one time per week.
Now launch the Kaspersky Anti-Virus Scanner. It´s time to configure it.
Click in the "Expert" button at left side. (bottom)
"Options" should be configured like this:
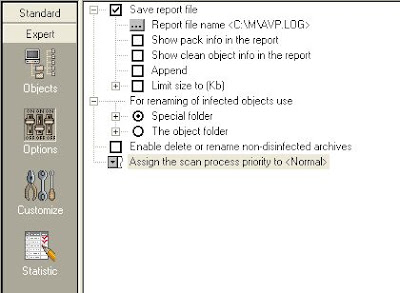
Just change the path of the report file to the one you prefer.
"Customize" should be configured like this:
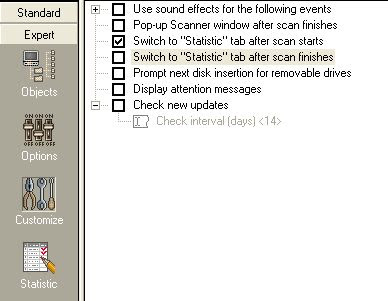
Now go the menus and click "File -> Save profile as default". Save the file in the same folder you installed KAV.
And that´s all. You have KAV ready to be used.
KAV can be launched from command line. The proper command line to use is:
AVP32 /S /W /Q C:\FOLDER_TO_SCAN
If anyone has any doubt just drop a comment.
lunes, 20 de julio de 2009
Overview of how to sort a malware collection and the tools involved in the process
It´s time to start talking about how to sort your malware collection and presenting the tools you will need in the process.
The first needed tool is the antivirus you will use to scan your collection. You will use KAV 4.5 as I already commented in a previous post in this blog. Using it we will be able to get a list of the malwares we own. You may use other antivirus but for malware exchanges KAV is the standard.
The second needed tool is a software that builds databases from KAV logs. This tool is named VirSort 2000, better known as VS2000. The tool will be explained more deeply in a separated post because it has a large list of functions.
A malware collection is just a bunch of files, so rest of tools involved in managing a malware collection are related to processes related to files.
In a malware collection we must avoid having duplicated files. For this task a good tool is FWeeder by Bumblebee.
Malware collectors usually store the files in their collections by a hash. Years ago CRC32 was the most popular. Years later was MD5. Actually collectors still use MD5 and others use SHA-1 or SHA-256. Having the correct extension for every file in the collection, even if it may be dangerous, it should be a good idea. For all the renaming tasks RenFiles is the tool.
When you trade you must deal with the files the other trader requested. StripLog is the tool for this task.
The above tools (KAV, VS2000, StripLog, RenFiles and FWeeder) are in the basic collection kit of any trader.
Other tool of interest could be VxUnpacker, the tool coded by MoRRo to decrypt quarantined/crypted files. And another one would be VS2000 GUI which is like a compendium of VS2000+StripLog+RenFiles and it can be used for other tasks.
I will dedicate one entry of the blog to every tool.
domingo, 19 de julio de 2009
How malware collectors exchange
Today I will explain the basics of how malware collectors exchange, but before I must explain a few things to understand why things are done the way they are done.
Many years ago someone, I don´t know who had the idea, thought that to exchange viruses the best way was to use logs (reports) created by antivirus products to know exactly what everyone had in his collection. As antivirus usually give an unique identification for every variant of every virus family this was a good method. So collectors picked 3 different antivirus (Dr. Solomon, F-Prot and AVP) and they used the logs created with them to exchange.
Obviously it was necessary to create tools to process logs: create databases from your own logs containing unique variants, generate reports with the missed stuff from the logs of other traders, .... but that´s stuff for other day.
A few years later Dr. Solomon became very slow scanning and after a time it was dropped by collectors as common used antivirus for the exchange. F-Prot was also dropped because its ability to detect unique variants decreased. So AVP remained as the only one commonly used antivirus to exchange.
Even if AVP is the best antivirus detecting known viruses and malwares, collect using only one antivirus was not a good idea so for a while collectors used from time to time other antivirus to exchange: Nod32, BitDefender, AVG, McAfee, ...
Two years ago, more or less, the amount of detected malware started to increase exponentially. Since then using several antivirus to exchange became a very difficult task for collectors having big collections. Lots of scanning hours would be required to generate logs. That´s why usually only AVP is used to exchange between big collectors.
As anecdote I should comment that never ever a woman became a known virus collector and there were only a few virus writers, being probably the best known one Gigabyte.
Every collector may have his own rules to exchange, but everybody use KAV 4.5 Personal Pro in english to generate the log of his collection. You can find it here.
Most collectors update KAV definition databases from here. This is done because identification names change often. Two collectors using different KAV defs may request stuff they already have. The solution to avoid this situation is using same defs.
Years ago collectors may generate new logs every day. Actually that´s not possible because the time required to scan must be up to 48 hours if not more depending of the hardware resources. That´s why nowadays collectors generate one log per week so exchanges are done once in a week.
Between big collectors the exchange ratio is 1:1. It means that for every file you send, you receive other. Many years ago the used ratio with small collectors may be 3:1 or a different one depending of the trader.
Other golden rule is that the most veteran trader receives his request before sending the request of the other trader.
Personally I have next rule: I exchange viruses/worms for other viruses/worms and malware for malware.
And that´s basically how collectors exchange.
Resuming:
1) Update KAV defs.
2) Generate log with KAV 4.5
3) Create database from log.
Then you are ready to get a log from other trader and verify if you need anything from him. If you do, you send your log to the other trader so he can check if he misses something from you.
Pretty simple but effective.
It´s good idea that before starting to transfer files both traders are sure they are using same defs.
Next blog entries will be dedicated to present the tools commonly used to collect and keep the collection in good shape.
viernes, 17 de julio de 2009
Presenting other traders
Today I will present other traders. The few active remaining ones.
Baptist
You can reach him visiting his web site at: http://66.232.119.78/~largefus/
He has been collecting for a few years but his collection is very large.
He has contributed to the virus exchange community providing web space to allocate other collector logs.
Status: Active trader
Morro
He has been in the trading scene for long time, not as much as me, I´m kinda a dinosaur, but really a lot.
His major contribution to the collectors has been VxUnpacker, a tool coded in .NET used to decrypt quarantined/crypted samples. It´s the best tool in its genre so far. (and the only one)
You can reach him writing a mail to morrovx@gmail.com
Status: Active trader
MasterRat
He is the owner of www.megasecurity.org, a very famouse trojan repository.
You can contact him at masterrat666@yahoo.com
Status: Active trader
Vir Albb
Trader from China.
You can reach him at viralbb@yahoo.com.cn
Status: Probably still active
VirusTrader
Other trader from China.
Contact him at virustrader@126.com
Status: Active trader
SnakeMan
He is an australian collector.
You can reach him at snakeman@netspace.net.au
Status: Probably still active
Trney
He has been collecting for long time. He comes from Japan.
You can take a look at his website here: http://www5c.biglobe.ne.jp/~TRNEY/
Mail of contact: yk442311@kjb.biglobe.ne.jp
Status: Probably still active
White Master
You can visit his web here: http://whitemaster.pisem.net/
Mail of contact: whitemst@yahoo.com
Status: Probably still active
Seak
Visit his web site here: http://www.numentec.com/aver/seak/
Mail: seak@numentec.com
Status: Probably still active
A few months ago there were other active traders but lately I didn´t hear about them so I don´t know what´s their status. A list of them follows:
Senna Spy
Brazilian virus collector.
Mail of contact: sennaspy@uol.com.br
Germano
Italian virus collector.
Mail of contact: gdalessandro@gmail.com
Virax
Mail of contact: virax@gmx.co.uk
Apoc
Mail of contact: aappoocc@walla.com
VirusP
Collector from Greece. Owner of the site: http://www.virus.gr/portal/en/
Mail of contact: collecting@virus.gr
Zordhak
Mail of contact: zordhak.vx@gmail.com
And here it goes a list of other traders from the past. If any of them reads this he probably will be happy knowing there are still someone that remembers him.
Poltergeist, Shadow Seeker, Jack the Ripper, omega666, Galar, Danielle Fogazzi, Sokrates, Malware, Perikles, Newton, Zulu, Phage, Tally, HomeSlice, SlageHammer, Roadkil, Stramonium, GG-Nome, Raenius, Algol, NFission, Staggle, Specter, Quilb, BasketCase, ByteSurgeon, BaidareW, Nexus Crusader, Panoix, CyberWarrior, BlackCat, Szule, Vein (the craziest collector ever! ;), C-urtis, Toxic, Van Blue Fish, Zelgadis, SnowBlaze, Nemesizz, Dr. Rave, sphinx, Asad, Brian_Perl, Vortex, m0n30 (espero volver a saber de ti algún día ;), BuddyMusic, mr-virus, Akap, VirusJoe and CTDummy.
Sorry if I forgot someone but my memory is not what it used to be. O;-)
There are others but as we say in spanish: valgo más por lo que callo que por lo que digo. They know who they are. };->
martes, 14 de julio de 2009
Presenting myself (Part II) - Objective of this blog
I will start this blog entry replying the pendant question from previous post: Why is not possible nowadays to become a traditional collector?
The main reason that makes it not possible is because malware collectors have very large collections, containing over 400k and 500k unique samples, therefore someone that starts collecting can not join the trading game.
Obviously anyone can collect malware but not at the level that traditional collectors reached.
Continuing with my presentation...
Between 1994 and 1996 I was related to BBS, specially Dark Node, the BBS where I was SysOp, and Internet. In 1996 Dark Node closed and since then I have been related to the virus/trading scene through Internet.
Since 1994 I exchanged viruses with other collectors at Internet. I also got new viruses directly from virus coders. Being a 29A member helped me greatly to get new stuff.
Around 1998 I created a website dedicated to the virus exchange and the virus scene in general. I named it "Virus Trading Center".
Not much time later I thought it would be a good idea to create a small group formed by the best collectors, so I explained my idea to ShadSeek, Slage Hammer and Tally. They agreeded and we formed a group we named "Virus Trading Group". Some time later Cicatrix also joined to the group.
As IRC was the meeting point for virus collectors, around the same dates, in 1998, I decided to create my own IRC channel. I named it "vx-vtc" in reference to virus trading center.
For long time most of the collectors of the world joined there to meet and arrange exchanges.
But things don´t last forever and after two years, more or less, internal problems inside Virus Trading Group leaded to split up the group. Some collectors also decided to leave vx-vtc IRC channel and create their own channel.
Anyway the period between year 2000 and 2006 was a good one for exchange. As I commented in previous post, collectors came and collectors left. Some of them were good friends and we had a nice time trading together. Spending time at IRC chatting about anything was the real fun of collecting.
From 2006 until today the number of collectors have been decreasing. Old collectors like VirusP left the trading scene and nobody came to replace the empty places.
2008 was the year when collectors definetively left IRC as meeting point.
A few years ago I closed Virus Trading Center website and decided to create a forum for malware collectors. I named it "Malware Collecting Forum". The forum was probably created a bit late. It appeared when only a few collectors were remaining. The participation in the forum was so low that I decided to close it to the public.
I always liked to be connected in some manner to other collectors and share with them my experiences, my tools, ... First I did it through my web site. At the same time I created an IRC channel. After my site closed I created a forum for collectors.
Right now IRC channel still exist but nobody joins there. Website is gone and forum too. So I decided to give a try with a blog.
What´s the objective of this blog?
I will bring here the malware collecting procedures I consider the right ones. I also will comment the tools (third part or my own ones) to do collecting tasks.
That´s more or less what you can expect from this blog. Anyway I´m open to critics, suggestions, whatever. So don´t hesitate to contact me and send your comments.
jueves, 9 de julio de 2009
Opening the blog. Presenting myself (Part I)
I will present myself in this first post of the blog.
I´m VirusBuster, a malware collector. I used to define myself as virus collector, but nowadays viruses are so rare (almost everything are malwares) that some time ago I decided it would be fair to change the "label" from virus collector to malware collector.
I´m from Spain and I have been collecting viruses and malware since 1992. It was in that year when I met someone that introduced me to virus collecting. He had a small collection of viruses, and after the initial shock (who could be so insane to keep them?), I was truely interested about them.
At the beginning I used to get new specimens from pirated software, but after a time always the same viruses were showing up. Then, how to get new viruses?
In that year, in Spain, BBS (Bulletin Board System) were the most used way for communications. Internet was something reserved to universities yet, so I started my quest for new viruses in the spanish BBS. After a time I located a BBS with several new viruses and something that was like the grial, the Virus Creation Laboratory (VCL). I sent my viruses and just in a few days I got access to all the viruses. Chiba City rules!
I joined (in 1993???) Fidonet just to get access to VIRUS.R34. I met there other people interested in viruses, in writing and collecting them. After a time some people complained because they considered that publishing virus codes was not politically correct and after some argues exchanged the moderator decided to ban that kind of stuff. In that moment I and the person who introduced me to virus collecting, decided we should create our own BBS dedicated to anything related to viruses: coding, collecting, ... That´s how Dark Node BBS was born.
Very talented virus writers joined the BBS, most of them coming from VIRUS.R34. It was a common project so they helped economically to buy the required hardware.
After a time, using stuff (articles, virus source codes, ...) published in the BBS, a virus magazine, in the style of Immortal Riot and Vlad, was created. It was called 29A #1 and a virus group, formed by members of the BBS, named as the magazine was created too. What happened with 29A... is other story.
From Dark Node times I keep nice memories, specially about the meetings we did.
In 1994 I got internet connection at home. A common friend of a friend got us internet access using a modem installed in the university as bridge. I still wonder how the hell he did that.
I don´t remember where I heard about IRC but the question is that I joined #virus at Effnet and met there most of the greatest collectors of that time. Poltergeist, Shadow Seeker, jtr, omega666, Danielle Fogazzi, ...
They teached me their procedures for virus exchange and shared the tools used in the process.
My collection compared to the collections they had was a joke but I decided I would be patient and constant. Keeping that in mind it was not a surprise that with the years my collection grew a lot. I also learned that being honest and loyal, keeping promises (and also secrets) and being a nice person, was the key to be a better collector.
With the years collectors came and collectors left.
I can say with the heart on the hand that the best thing from all these years of collector has been meeting and knowing other collectors. The list of collectors to greet would be too large so I´ll just say: Kind regards for Perikles and the rest of collectors I appreciate.
As a person who likes to question things, there was a moment I asked myself: What´s the meaning of being a virus collector? Is all about a file exchange? Send and receive?
I didn´t think so. For me virus collecting was teaching how to collect and helping to new collectors, as previously other people teached me, specially Poltergeist, who I consider my "father" in virus collecting. Poltergeist was the model I used as mirror. He was the kind of collector I wanted to be when I joined internet and met other international collectors.
Therefore apart of trading files, for me collecting was helping other traders, guiding them in their first steps as traders. But there was other important thing...
From very old times, collectors used antivirus to make reports and use those reports to know what they had and what they missed from other collections. A few tools were created with the purpose of exchanging viruses but the most famouse was VirSort by Jim Fougeron (Poltergeist), originally created by ShadSeek.
When Poltergeist left the scene he sent VirSort source code to Spooky but he never released a new version. Then ShadSeek created a new virus collecting tool named VS2000 (VirSort 2000). After a time he also stopped development of his tool and that was a shock because I was used to use other people tools. Who would continue developing the tool and adding new features?
I wanted to add new functions I considered important for collecting so I asked ShadSeek a copy of VS2000 source code so I could continue developing it. I had to learn Pascal for this.
That´s how I discovered another important aspect of being a virus/malware collector: the tools for collecting. With the appropiate tools collecting is easier.
Actually if someone asks me "what makes of someone a real virus/malware collector?" I know the answer. My answer.
For me a true virus/malware collector, in the traditional sense, has next characteristics:
* Someone who is able to get many new samples in a constant basis.
* Someone that has the knowledge to help other collectors.
* Someone that rarely infects the system because stablished controls to avoid that.
* Someone able to code the required tools for the tasks involved in collecting.
Becoming a true collector is something that takes time and effort.
I consider that nowadays becoming a traditional collector is not possible anymore. The reasons for that is something I will comment in next post.
End of presentation. Part I.